Resource Center
Welcome to the PRTG Resource Center where you'll find all of our great content at a glance.
Happy reading and watching!
PRTG product brochure
PRTG empowers system administrators to monitor their entire IT infrastructure.
Check out our product brochure to get a concise overview of the features, functions, and benefits of PRTG.
Email course on bandwidth monitoring
Monitoring your bandwidth helps to ensure availability of your IT infrastructure. There are four methods: SNMP, Packet Sniffing, Flow and WMI. In our 6 part course, we'll explain how they work and when you should use each one.
Ping Speed Test
How fast is your web server, really? Our Ping Speed Test will check your ping times from five different locations.
Speed up your website
Wait? Don't wait? Clients decide within seconds. You think good things come to those who wait? Well, try to tell your clients when they're gone. If your website fuels your business financially, poor performance can quickly become a sales killer.
9 ways to avoid common network issues
We provide you with 9 tips to avoid common network issues and ensure the daily health of your systems.
How to choose the right monitoring solution
A good network monitoring solution is essential for a healthy and stable network. But which one is right for you? Our white paper provides you with an explanation and the selection criteria to help you decide.
Solve everyday network issues with PRTG
As a system administrator, our colleagues, supervisors, and customers look to us daily for answers to common questions, like "Why is my email down?". We provide you with 11 solutions to everyday network issues.
Monitoring applications and services
Company productivity in today’s IT age is heavily dependent on the applications and services used within the company.For this reason, these applications and services should be monitored. But how?
Network management tool consolidation
Network management tool consolidation is essential for effective IT operations. This means managing your infrastructure centrally instead of using multiple tools.
SNMP email course
Monitoring with SNMP is essential for anyone responsible for servers and network devices, such as hosts, routers, hubs, and switches. Our 4 part course on how to use SNMP for network monitoring will help you improve your network operations.
Learn all there is to know about SNMP
IETF1 developed Simple Network Management Protocol (SNMP) towards the end of the 80s, and it is still in use today by many devices. But why is it still the standard? What are the alternatives? And what does the future hold for SNMP?
Putting SNMP into practice
Our second SNMP White Paper focuses on the technical aspects - from the use of MIB files to the practical setup of network monitoring. We also take a look at some of the inadequacies of SNMP in modern networks.
Monitoring of private clouds
The private cloud - just like any other cloud - depends on the efficiency and stability of the IT infrastructure. This means your network monitoring strategy is vital. Learn more about monitoring the private cloud.
Cloud Roadmap
What are the reasons to move to the cloud? How do you handle the migration to the cloud? And how do you minimize stress and mitigate the risks of a migration? Find all these answers and more in our Cloud Roadmap E-book.
The IT administrator's communication pack
Good communication is a must for any IT administrator to keep things running smoothly. Download our communication pack and get email templates for common scenarios, as well as some general communication advice.
IPv4 subnets cheat sheet
What a great subnet mask! Do you know how many addresses are available in this subnet? What about the Classless Inter-Domain Routing (CIDR) notation? And what is .224 in binary?
IPv6 subnets cheat sheet
Do you know the different types of headers IPv6 offers? What are the ICMPv6 error message types? And which header field is used by OSPFIGP? Don't panic, you'll find all the answers in our IPv6 cheat sheet.
Help on common error codes and messages for sysadmins
As we want to make your life as a Sysadmin as easy as possible, here's a small dictionary of the most common error codes, problems and messages caused by your systems you probably have to deal with from time to time.
The periodic table of network monitoring
Our team has developed a new overview on how to illustrate the most relevant terms and terminology of system administration. Categorized into various groups, you’ll find everything from Ai for API, Rt for Router, to Wm for WMI.
IT onboarding script
New hires, new challenges. Our onboarding script can save you time and energy, and you’ll be less likely to forget a critical step, like organizing a workstation! The script automates a load of standard procedures.
IT offboarding script
Our offboarding script helps you make sure that employees don't just leave the company; they also leave your system!
Monitoring for start-ups
Even start-ups need to monitor their IT infrastructure, since it is one of their crucial business success factors. Learn more about monitoring your start-up here.
The ultimate guide to network mapping tools
Up-to-date and detailed network maps can be indispensable to IT managers. Here are 9 network mapping tools that we reviewed in collaboration with an independent institute.
Network monitoring and risk management
We examine the risks facing IT and, in particular, network operations, and provide a three-step approach for creating an IT operational risk management strategy.
Central monitoring in distributed systems
Organizations with infrastructure at multiple sites need to keep track of the network at those locations. Find out how PRTG Network Monitor can be extended to additional locations using Remote Probes.
Software evaluation based on consumability
The abstract concept of the "consumability" of technical products was conceived by IBM for product development. But how can it be helpful in evaluating software - specifically network monitoring software?
How to get the IT budget you want
With worldwide IT spending being on pace to total $3.5 trillion in 2015 (Gartner, 2015) - why does it feel like you can never get the budget ...
5 questions to help you find the right monitoring solution
Choosing the right network monitoring system for you is a case of asking the right questions.
ROI calculation for network monitoring software
„Return on Investment“ is intended to provide a simple calculation that determines the period during which an acquisition is amortized. But how does this apply to network monitoring software?
How to boost understanding of IT security
Here are 13 ways that you can raise security awareness in your organization, including what technical measures you need to take, and what to do if it's already too late.
Meta Security - Is your security really secure?
Many hot trends in IT follow the trajectory of a firework on the Fourth of July: A loud bang, burst of light and it's over. Security is not one of those trends. Since the early days of networking, IT-security has been a critical issue, and that remains true now more than ever.
Shadow IT - lurking in your network
Shadow IT is IT that is used outside of the official infrastructure of a company or without clearance from administrators. From private smartphones, USB sticks, to new cloud services: Shadow IT takes on many forms.
Why you should consider server virtualization
How does virtualization work, and how does it affect network management?
IT monitoring in hospitals
The recent digitization of healthcare IT has led to medical devices, medical data systems, and the traditional IT infrastructure becoming intertwined. Learn how to monitor the new integrated medical landscape.
Healthcare IT - a monitoring primer
This primer introduces some of the core systems of a healthcare organization and introduces best practices to ensure a complete and reliable monitoring solution specifically for healthcare IT infrastructure.
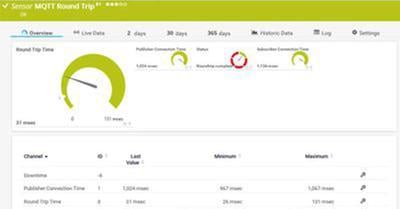
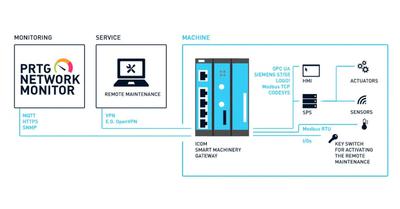
Native sensors to monitor industrial environments
PRTG not only “speaks” all common IT protocols and languages, but also offers native sensors for universal protocols like MQTT or standards like Modbus TCP and OPC UA.
Industrial Network Security
PRTG industrial brochure
Free White paper: IT/OT convergence
In modern industrial IT, the right teams need the right data. Our guide shows you how to implement holistic monitoring that brings elements from IT, OT and IIoT into your dashboards.
Paessler recommended partners in Industry
Our selected partners worldwide have the industry-specific knowledge.
Professional consultants will guide you on your journey towards a holistic industrial monitoring solution.